Document sharing



by iago.soto | We were exhibiting at the MWC Shanghai last week, the Asian edition of the GSMA MWC Barcelona, organised . This was the first edition of the summit, previously called Mobile Asia Expo. We had a booth at the Mobile World Capital Barcelona, the public institution that tries to boost Barcelona as a…

Sippo is the name of a WebRTC product family authored by Quobis which includes the following products: Sippo WebRTC Application Controller (or Sippo WAC): the server which provides the services. Sippo WebRTC Apps: reference web applications which leverage the main features provided why the WAC. Two current application available: Sippo Web Collaborator: Reference enterprise WebRTC…

How long does it take you to get to the office?and visiting customers? what if it rains or there are traffic jams, How much time did you spend in transit? It seems that Elon Musk is not a fan of a world full of time inefficiencies. So much so that Zoom during “Zoomtopia” announced that…

What is a “Gatekeeper” according to the DMA: Any company providing any of the previous services is potentially bound to this law as long as it meets some sizing criteria to be considered a Gatekeeper. The threshold to meet the Gatekeeper condition are:: Having a yearly turnover of €6.500 millions or higher in the EEA…
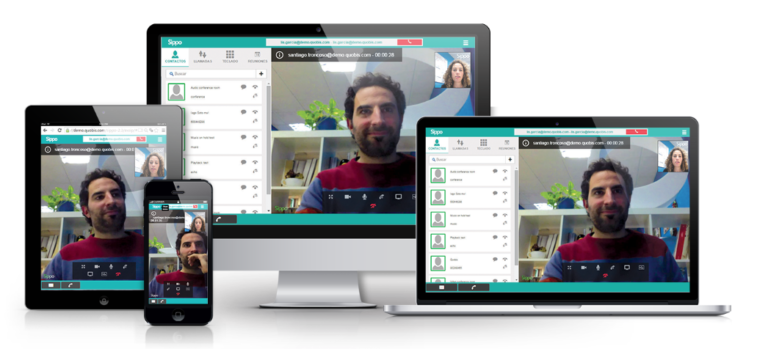
The future of communications is changing. In the last few years, instant messaging, live chat or webinars have become an everyday tool for millions of users. Because of this, having an omnichannel communication strategy is crucial to engage customers, build brand awareness and differentiate from competitors. Video represents an opportunity for companies to develop innovative…
SIPREC the most used call recording protocol SIPREC is currently the most widely used call recording protocol. It is based on a protocol defined by the IETF and massively adopted by interconnection elements such as SBCs (such as Oracle, Ribbon or Audiocodes) and call recorders. The standard under RFC 7866 was promoted by Nice, Verint, Cisco, Unify (now…