Branded Calling
All you need to know about branded calls

Branded calling: a big step toward restoring trust in the voice channel
Branded calls represent a great opportunity to restore trust in the voice channel and improve responses to legitimate telephone contact attempts by companies and organizations.
Modern branded calls are closely linked to the evolution of call authentication processes. As you can imagine, identifying calls with logos, brand names, etc. would be of little use if it were possible to easily impersonate a brand. Trust in branded calls depends on the ability of operators and companies to ensure that these calls are indeed from who they claim to be.
On this page, we will take an in-depth look at the state of the art of branded calls, understanding the motivations and obstacles behind this revolution in the telecommunications industry.
Introduction
What are branded calls?
The simplest explanation is that branded calling involves presenting brand information (such as a logo, name, or other information in addition to the phone number) on the recipient’s device when they receive a phone call from an organization. This information allows the recipient to correctly identify the caller and make an informed decision about whether to answer the call.
Anatomy of a branded call
The way branded calls are delivered depends on the framework they’re integrated into. For example, they won’t look the same in China (Chaken) as they do in the US (STIR/Shaken). But to get a rough idea of what’s meant when we talk about including branded calls in a call, let’s start with the CTIA (Branded Calling ID) paradigm, the “de facto standard for branded calls in the US, based on Rich Call Data.
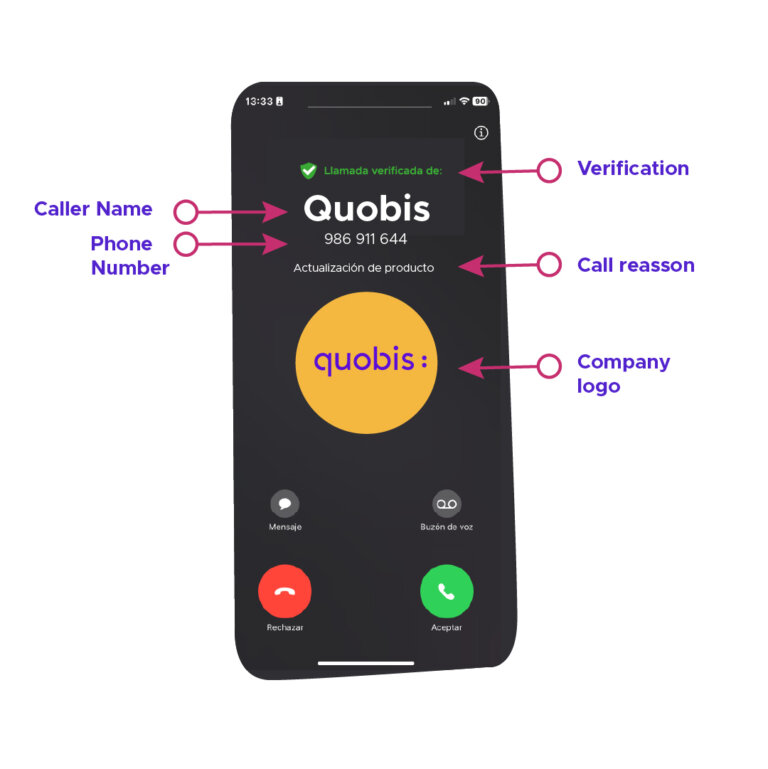
Content of a branded call based on RCD
- Caller display name: This is the name the brand displays on the consumer’s phone when they make a call.
- Phone number: The caller’s phone number. It may display an icon justifying that it has undergone a vetting process, ensuring its legitimate use by the caller.
- Call reason: A short text describing the reason for the call (e.g., scheduling an appointment, commercial information, orders, etc.)
- Company logo: The image of the brand making the call. It will generally have undergone a verification process by the Branded Calls partner, in which the brand has demonstrated that it has the right to use it in its communications.
- Verification: In this example, the STIR/SHAKEN framework implies that the caller’s information has been signed and authenticated by the originating operator, so it cannot be subsequently modified.
Precursors of branded calling: history of telephone caller identification
Current caller ID solutions promise higher standards in calling party authentication and verification, thanks to the introduction of technologies such as digital signatures, certificates, tokens, etc. Furthermore, the evolution towards IP networks allows for more information to be added to calls and includes resources such as Rich Call Data (RCD), which results in a richer and more informed call experience, with the consequent improvement in trust for the recipient.
Milestones in caller IDentification
1970
First prototypes of caller identification technology (Paraskevakos).
1980
1981 – First residential caller number identification service (BellSouth).
The “International ISDN number” emerges
1990
“Caller ID blocking” appears.
Using centralized databases (CNAM) to add a name to the caller number
2010
eCNAM expands the capabilities of CNAME (allowing you to include your logo and other information)
Growing popularity of anti-spam solutions (Hello, Truecaller…)
CPaaS & SDKs
2020
RCD (Rich Call Data)
Telecom APIS (CAMARA)
2025
In this post, “A Brief History of Caller ID,” we take a detailed look at the major milestones in caller ID from the 1970s to the present day.
Technologies for branded calling
How Branded Calls Work: Branded Calling Technology Strategies
There are different frameworks and architectures that share the goal of presenting branded information to the called user. As we have seen throughout history, different technological solutions have overlapped over time. Currently, different solutions coexist, ranging from simply presenting the calling number to presenting a screen with information from multiple sources, such as the logo, reason for the call, the caller’s name, and verification of the call’s origin (attestation) by the originating operator.
Since the presentation of information is determined by the operating system of the destination terminals, the greatest differences are found in the previous steps of the value chain, especially in the verification and authentication processes.
In addition to the technological component, one of the key differences between the different architectures is the participation of different players in the ecosystem. While some involve the originating operator, the terminating operator, certifying entities, branded calling providers, etc., others only involve the terminating operator and a branding service provider; or they bypass the originating operator by starting from the corporate network and sending the information directly to the terminating operator through a third party that offers the branded calling service.
Caller ID transmission via FSK/DTMF (legacy environments)
Perhaps we can’t properly speak of branded calls, due to caller ID transmission via FSK (Frequency-Shift Keying) or DTMF (Dual-Tone Multi-Frequency) is more limited.
If it’s done via DTMF, it will only display the caller’s phone number, and if it’s done via FSK, it could also display a name. However, we considere it a forerunner ; after all, it covers the need to filter calls that the recipient wants to answer.
The caller ID service depends on the phone (i.e., the terminal itself or the user interface) supporting these data transmission formats. It also depends on the user subscribing to the caller ID service offered by the operator.
Caller ID transmission between the first and second ring (source:: ResearchGate)
Caller ID transmission via SIP (VoIP)
For caller ID in VoIP environments, a series of SIP headers are used in the SIP INVITE message (the SIP INVITE request is the message sent by the calling party, inviting the recipient to a session).
INVITE sip:+14085551212@gw.pstn.net SIP/2.0
Via: SIP/2.0/TCP useragent.cisco.com;branch=z9hG4bK-124
Via: SIP/2.0/TCP proxy.cisco.com;branch=z9hG4bK-abc
Via: SIP/2.0/TCP proxy.pstn.net;branch=z9hG4bK-a1b2
To:
From: "Anonymous" ;tag=9802748
Call-ID: 245780247857024504
CSeq: 2 INVITE
Max-Forwards: 68
P-Asserted-Identity: "Cullen Jennings"
P-Asserted-Identity: tel:+14085264000
Privacy: id
IETF RFC3325
Name supplied with the following headers, in order of priority, starting with the highest priority:
- P-Preferred-Identity User (PPI)
- P-Asserted-Identity User (PAI)
- Remote-Party-Id User (Remote Party ID)
- FROM User (Contact)
For example, when both the FROM User header and the PAI header are present in a SIP INVITE, the PAI header takes priority and is displayed as the caller ID number due to its higher priority.
Manipulating the Caller ID Display
SIP message manipulation can be legitimate or illegitimate. As it is software, it allows the caller ID manipulation process to be scaled and automated, allowing for massive and sophisticated attacks to be executed.
An example of legitimate caller ID manipulation occurs when a local device (such as a PBX) and a telephone service provider use a different numbering format. In this case, an operator might use the E.164 format, following the international numbering plan, while the local network might use a different numbering format.
This same flexibility opens the door for a malicious actor to modify caller information (spoofing) to impersonate an entity (a bank, for example) for the purpose of carrying out telephone scams.
Phone call identification using CNAM / eCNAM
CNAM is the first modern approach to branded calls, as it involves a conscious attempt to present the brand to a customer for branding purposes (improving brand perception, generating differentiation, etc.), although on a technical level there are important differences with more current alternatives such as those supported by RCD.
CNAM stands for Caller ID Name; it literally displays a name to identify the caller alongside the phone number. For businesses, CNAM “guarantees” that their brand name is correctly displayed to their customers. This transparency reduces the possibility of the message being flagged as spam. This is especially important for businesses that rely on outbound calls for sales, support, or customer service.
A number’s CNAM can represent a limited string of characters (approximately 15 in the case of CNAM and approximately 35 in eCNAM) and is presented in capital letters as a standard industry practice. Other CNAM conditions:
- It cannot begin with a number; it must begin with a letter.
- It can only contain letters, numbers, periods, commas, and spaces.
- It must be a unique name or value; it cannot be a generic value such as city or state.
CNAM is available in the United States and, with some limitations, in Canada (Puerto Rico). It may require the recipient to have CNAM services enabled on their phone plan, which may incur a fee for this service on incoming calls.
To display the name assigned to the caller’s phone number, the destination carrier must query databases containing these CNAM data entries. These databases are known as CNAM repositories, and collectively (since there is a wide range of providers offering this service) as LIDBs (Line Information Databases).
What evolution does the enhanced CNAM propose?
According to the Federal Communications Commission (FCC), eCNAM will help users manage their calls by providing additional information beyond a “name.”
eCNAM is an American standard (ATIS-1000067.2015) that leverages the capabilities of NGN IP networks to provide greater information about the origin of the call. It provides a full name (up to 35 characters) and can add additional information about the caller to the SIP headers of the call information. This additional information is obtained from authoritative databases that can provide information about whether the call is spam or robocalls, or whether the origin is untrustworthy.
Reputation databases and antispam applications
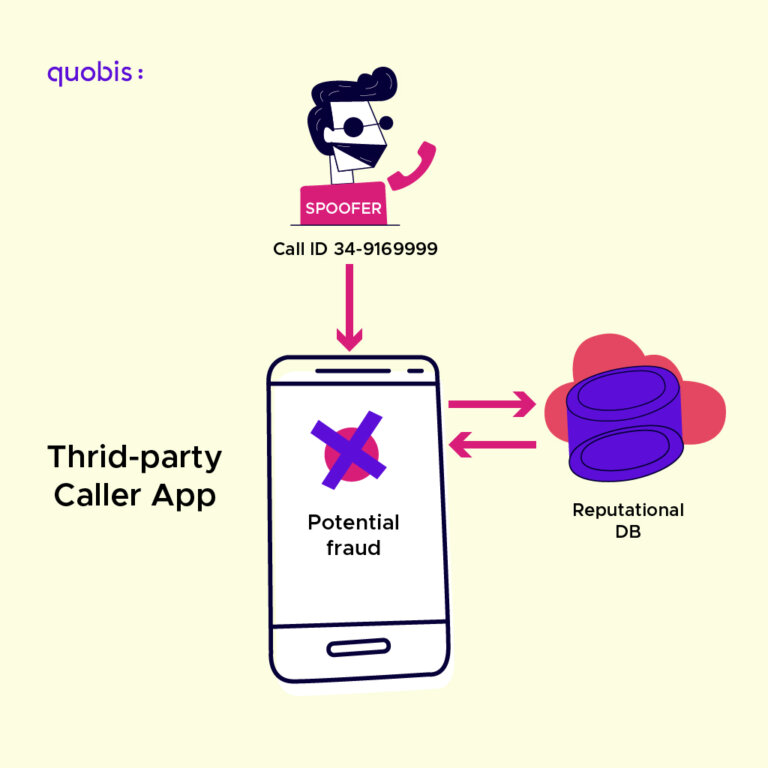
Anti-spam apps such as Hiya, Truecaller, and similar applications have leveraged the technical capabilities of smartphones to offer one of the first rich branded calling experiences to users, under the premise of combating phone spam and fraud.
Basically, these are apps that the user (recipient) installs on their device, with permission to interact with ongoing calls and even block them if they meet certain exclusion criteria. The filtering, labeling, and caller ID processes are shared between the user’s device and the cloud services of the provider of these solutions, without interacting with the operators involved in the call.
Antispam applications and terminal manufacturers
Driven by the growing interest in combating spam and phone fraud, these services have expanded significantly, taking on highly influential positions in the industry. For example, we’ve seen some manufacturers reach agreements with them to offer them as standard in their Android distributions (i.e., Samsung Smart Call); also to their credit, Apple has introduced new capabilities for these applications (i.e., Live Caller ID Lookup), and even Google descontinuating its own solution in 2023 (Google Verified Calls), leaving the field clear for these identification service providers to focus as device manufacturers on other strategies to improve the telephone experience, such as AI-based call screening solutions.
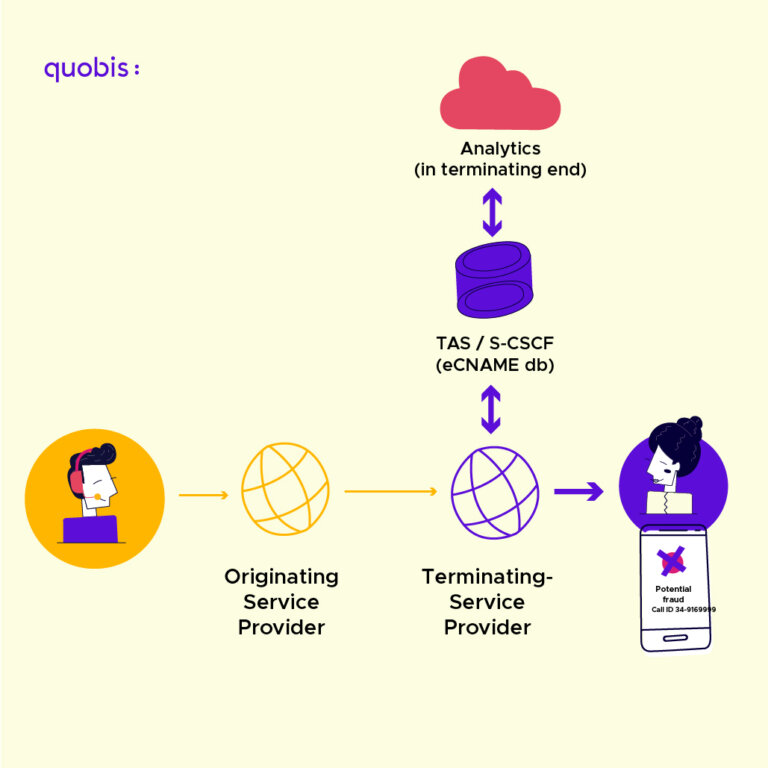
Reputation databases and antispam solutions in operator networks
New regulations are putting increasing pressure on operators, who must be proactive in curbing spam and phone fraud on their networks. In this context, the analytical tools of these solutions and the accumulated intelligence have direct applications in operator networks.
Currently, some of these providers are integrating into branded calling ecosystems in the telecommunications industry, such as Branded Call ID, to become onboarding agents, contributing their expertise in providing rich content alongside brands.
Quobis Caller Score
Operator-class solution for assessing the risk of each call in real time.

Branded calls using Rich Call Data (RCD) on STIR/Shaken:
We can define this solution as the first operator network solution to offer branded calls, without the need for third-party applications on the terminals. However, it is a technology designed to run over IP networks, which excludes calls made over legacy networks (although there are some out-of-band solutions on the table to make traditional networks compatible with branded calls, the reality is that they add more technical complexity to an already quite intricate process).
To simplify the explanation greatly, as an introduction, we can say that STIR/SHAKEN tells us whether the origin of the call has been verified by the originating service provider, while RCD (Rich Call Data) allows additional information, such as the name or logo of the company making the call, to be attached and delivered from a trusted source.
Therefore, this combination of STIR/SHAKEN and its standards, with its RCD extension (optional, since STIR/SHAKEN can be used without RCD), provides greater security and a more complete user experience in the calling process.
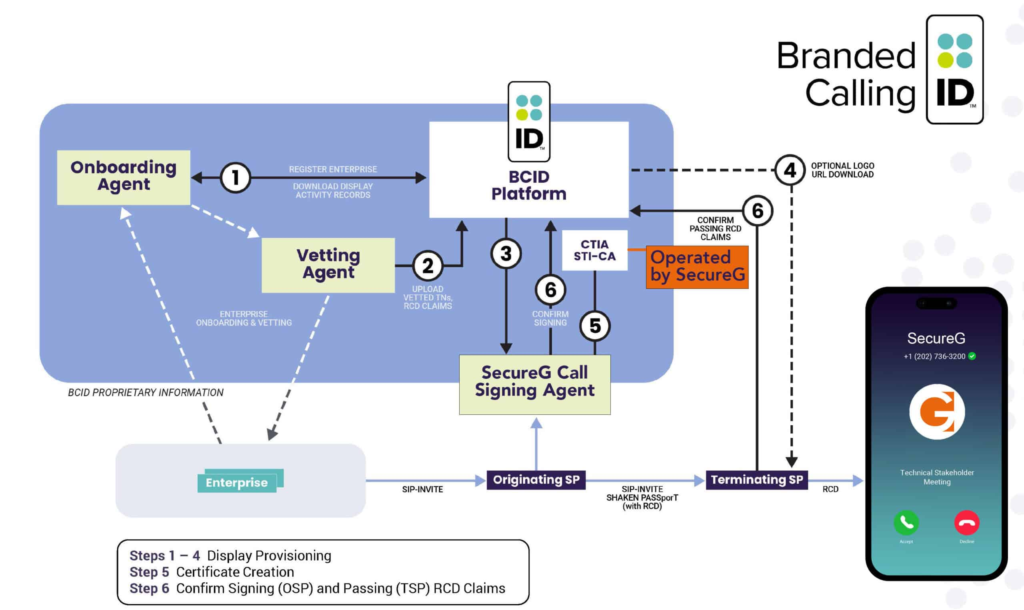
The Branded Calling ID (CTIA) ecosystem
The CTIA (Cellular Telephone Industries Association) has managed to recruit the main North American operators and a good number of branded call providers into its ecosystem, including some pioneers such as TNS or Transunion. Such is its level of penetration that it is the de facto standard for branded calling in the USA.
Out-Of-Band Branded Calling Solutions
Out-of-band solutions refer to all solutions that send part of the call information over a channel other than the primary channel.
In the context of branded or verified calls, we consider the telephone network as the primary channel, and secondary channels, such as communications via API or RCS messages. This is different from “in-band” call authentication solutions, in which both signaling and certificate information travel over the same channel.
Out-of-band, to add STIR/Shaken and RCD in networks with legacy elements (not VoIP)
One of the limitations of STIR/Shaken is its incompatibility with legacy networks. Out-of-band communications can help fill some gaps while the transition to IP for telephone networks is pending.
Some providers, such as Transunion, propose the use of out-of-band communications to deliver information regarding certificates and authentication/verification processes to the final operator. Similarly, it would be possible to integrate branding information via out-of-band communications through additional services.
Enterprise Call Authentication Solution
In this proposal, the originating operator does not participate in the authentication/verification of the call, but rather it is an element of the company’s network (originating) that communicates via API, with a verification and branding service, and this in turn with the terminating operator, who delivers the RCD to the receiving terminal.
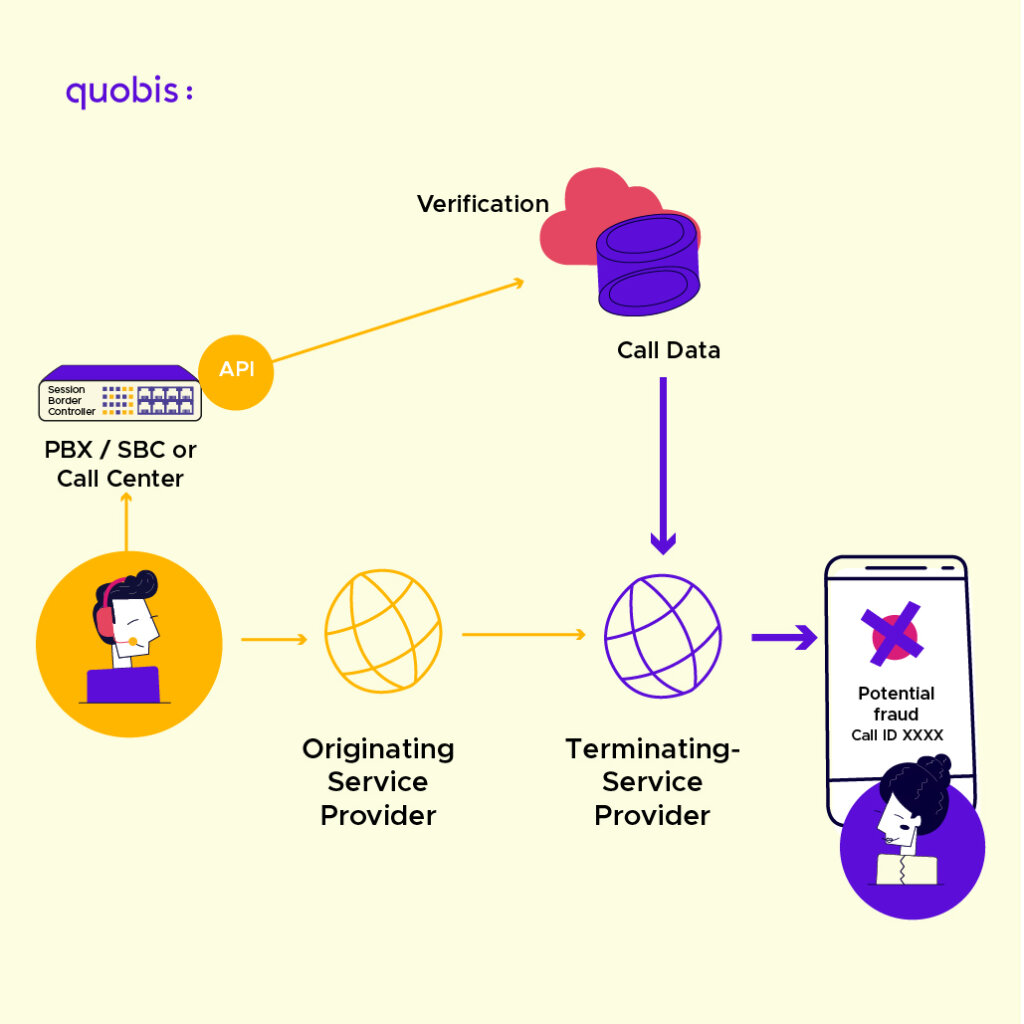
Operator APIs for call authentication and branded calls
Quobis is actively participating in the definition of several CAMARA project APIs, specifically WebRTC and Verified Caller.
The Verify Caller API, along with other APIs in the “Authentication and Fraud Prevention” category such as Number Verification, KYC, and more, allows developers to build applications that generate calls with different layers of security and value-added information such as branding.
Telecom APIS
Quobis helps telcos and enterprises take advantage of the apification trend in telecommunications.

CPaaS and Verification via SMS, RCS or Push Notifications
In the logic of generating events simultaneous to the call, to indicate to the user that the call they are receiving is indeed from a reliable source, the sending of SMS, MMS or RCS is perhaps a more universal solution. CPaaS act here as facilitators of the infrastructure necessary to scale through automation and integration with business apps, the delivery of these notifications, in a similar way to how 2FA verifications can be done today using codes in SMS.
SMS
In the case of SMS notifications, it is true that branding is reduced to using an alphanumeric alias that can provide more information than a phone number to the recipient.
SMS messages are not particularly secure; in many cases, they are not encrypted. However, laws such as Order TDF/149/2025 in Spain, or equivalent laws in other countries, are promoting mandatory registration in centralized databases of aliases used to send commercial communications. This provides greater certainty about the authenticity of the message with which the originating entity announces the call at the same time as the call is made.
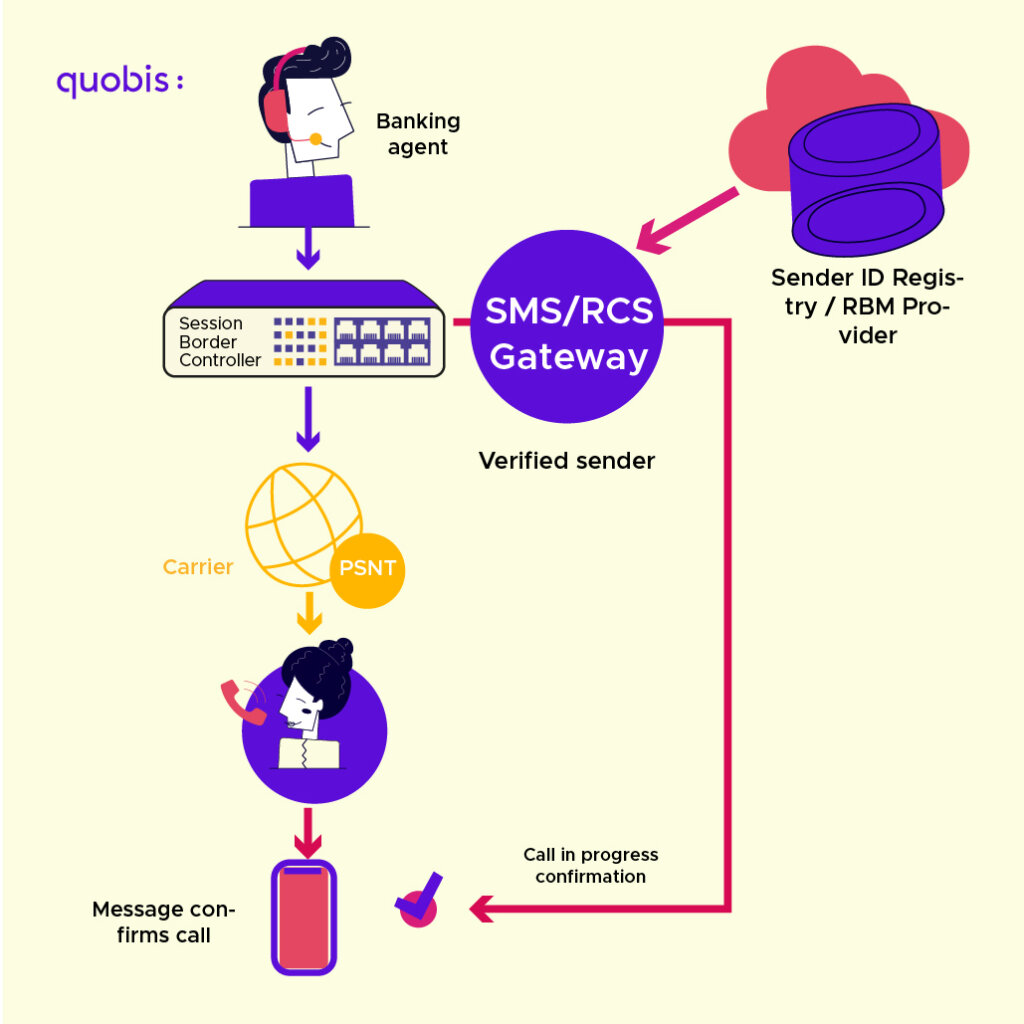
RCS / RBM
RCS stands for Rich Communication Services, and refers to IP instant messaging. RCS offers enhanced features such as multimedia file sending, read and write receipts, and group chats, all via data or Wi-Fi.
RBM, on the other hand, refers to RCS Business Messaging, which is essentially RCS geared toward B2C or A2P communications. In other words, it enables RCS so companies can communicate with their consumers, adding interactive multimedia messages (as click to call buttons) and carousels, enabling sender verification, brand customization, and providing metrics on these communications to companies.
Google leads the implementation and enterprise access to RBM globally, which in practice requires companies and partners to register and operate within Google’s environment, which is responsible for sender verification and RCS delivery.
Push notifications
Using an SDK from a platform like Quobis Communications Platform in a mobile app, it’s possible to notify the recipient simultaneously with the call (for example, by sending a push notification) that the brand is calling at that moment. This is a similar method to using RCS or SMS channels, but in this case, out-of-band event management is delegated to an app installed on the user’s device.
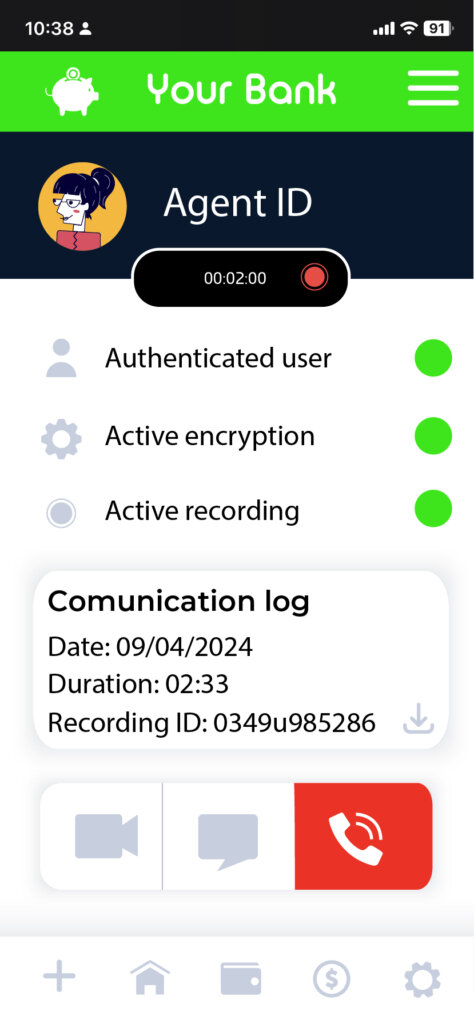
Embedded communications SDKs for branded communications
Embedding real-time communications provides the company with maximum control over the user experience. It allows for branded calls, independent of the telecommunications network, legal context or the agreements they have with manufacturers.
Having a brand app installed on the user’s device offers significant competitive advantages, especially when its customer penetration is high. One of these advantages is the ability to create a direct communication channel with the user. A user can also be fully identified through the native registration and login mechanisms, which is an interesting mutual guarantee, as it not only guarantees the authenticity of the caller but also of the recipient.
Calls can be made completely outside the telephone network, such as VoIP calls between the originating entity (for example, a bank) and the client’s application, which acts as a dedicated endpoint for communications between that specific company and its customers.
The call experience can be highly recognizable to the user. For example, using Callkit on iOS to create a slightly customized alternative interface to the call screen, with shortcuts to the app, a small icon of the company (or the installed app), and a descriptive text about the caller, for example. We can even customize the ringtone with the company’s jingle.
In addition, the company can benefit from the device’s MFA mechanisms to verify the identity of the user they are speaking with, or establish microinteractions to verify transactions protected with 2FA.
The main advantage of this strategy is that companies don’t need to wait for industry standardization, and the security layers provided by both the device and the app itself make impersonation by a third party truly difficult.
However, the disadvantage is that not all companies have a mobile app, or it isn’t widely available to their customers. However, in sectors where enterprise PPPs are widely used (e.g., banking, facilities, or, increasingly, the public sector), this option can offer significant opportunities and even significant economic advantages by eliminating operator costs.
Quobis Communications Platform
Our platform’s SDKs allow you to integrate advanced multimedia communications (chat, audio, video) into any application or website.
Why branded calls?
Why are branded calls important?
Organizations use voice communication for urgent and priority communications with customers, including resolving urgent customer service issues and discussing personal matters.
Voice remains the backbone of a successful multi-channel outbound strategy. While phone call volume continues to decline, 86% of decision-makers (Transunion 2025) believe it is the most important outbound channel for achieving customer service goals and increasing revenue.
According to data from Juniper Research, the total number of branded calls globally will increase from 1.5 trillion (US) in 2024 to 50 billion (US) in 2029. Global Newswire notes that more than 4,500 companies, including 15% of the Fortune 500, are already using a branded calling solution.
Enterprise-branded calls are a game-changer in outbound communication. The benefits they promise are as compelling as: increased response rates; improved customer experience; more effective calls; and ultimately, restoring trust in a voice channel that’s been subject to much abuse. Let’s take a look at what lies behind these promises and what other benefits they can bring.
Benefits of branded calling
Regaining trust in the voice channel
The telephone channel is essential for many companies to achieve their business objectives, but at the same time, we’ve seen call answer rates drop dramatically in recent years. Some studies suggest that 90% of business calls to consumers go unanswered because consumers don’t know who is calling.
How does branded calling build trust?
In a recent SIP Forum webinar on the challenges of branded calling, a representative from Hiya defined the concepts of “trust and security” for the branded calling industry this way:
- Business legitimacy: Ensure that the company is valid.
- Company representative legitimacy: Without this, any malicious actor could claim the use of a trademark that is not theirs.
- Content moderation: Ensure that the platform does not allow advertising language, insults, etc.
- Validation of ownership of the number Phone: Ensure that the phone number provided belongs to the company.
- Continuous Monitoring: Ensures that no company that was acting well before has changed its behavior and needs to be monitored again.
Customer Engagement
For what’s important, people prefer other people
Nearly 80% of consumers indicate that the telephone channel is important for communicating with companies. According to a 2021 study by Genesys, when consumers are asked what they value in customer service, empathy ranks ahead of speed of problem resolution.
The desire to speak to a person on the phone is a higher-value act for consumers when they need to discuss personal, important, urgent, or complex matters.
Improves contactability
It is a fact that branded calls improve contactability, and consequently, as consumers are more likely to respond, they will also benefit from the interaction.
If we analyze the main challenges to overcome when contacting customers, the following have been identified:
- Lack of response
- Failure to connect with the right person
- Spoofed phone number
- Old or inaccurate contact information
The first challenge is lack of response, and the causes of this are related to factors such as unknown callers, identity theft, consumer distrust of calls, or fraud. Branded calls reduce the need to multiply call attempts, reducing operating costs and improving business efficiency.
More balance between response rates and contact quality
Although many studies suggest that 76% of consumers are more receptive to answering calls with a name and logo, and others point to increases of up to 105% (TNS) in call response rates with Branded calls, the reality is that they don’t always have this direct effect. Let’s put it into some context then.
Answer rates may be reduced by branded calls, but this isn’t necessarily a bad thing. The reality is that we are allowing the target users to make more informed decisions when answering the call, which doesn’t mean they will always choose to answer our calls.
But if we focus on what happens with calls answered by involving branded calling, we will see very interesting benefits for brands. The first is that call duration increases:
- Avoid accidental responses or responses from uninterested customers.
- Interactions are based on brand recognition and greater trust in the channel, making conversations more productive.
- Effectiveness: Instead of wasting time attending to uninterested contacts, your team can focus on providing value to those who really need it.
Increases brand visibility
It’s almost obvious that including visual brand information increases its visibility, but it’s no small feat. Visibility is a source of brand recognition, putting brands ahead of their competitors when it comes to choosing a provider that meets a need that affects them, and is key to establishing brand loyalty.
More than half of those surveyed (Transunion) acknowledge that seeing information such as the name or logos on the mobile screen translates into a more favorable perception of the brand.
Fraud Prevention
Organizations that don’t identify their calls are more likely to be targeted by spoofing. Branded calls, accompanied by a reliable verification process, are an extra layer of security that improves customer confidence when doing business with the brand.
Avoid blocking by operators
Consumers around the world receive more than 81 million unwanted phone calls a day (Hiya), and operators are starting to label these calls to protect them.
In more and more countries, there are laws requiring operators to block calls that are not properly identified. Therefore, caller ID is moving from a “nice-to-have” value-added service to an unavoidable “must” in the medium term.
Legal framework for branded calling
Legal Framework and Self-Regulation in Branded Calling: USA, Europe, and China
Current regulations tend to focus more on mitigating robocalls and fraud than on protecting the integrity of branded calling.
Fighting against fraud requires a legal framework that defines responsibilities and provides tools to the different actors involved in the telephone call value chain.
The different legislative strategies range from the extreme of radical technological concretion (China, USA, France, etc.) to proposals for objectives related to the fight against telephone fraud, but with a more open approach regarding the “how” to achieve them (most European countries follow this strategy).
Regulation in ecosystems based on public key architectures and digital signatures
China supports its authentication CHAKEN with a national standard, “Technical Specification for Trusted Authentication of Caller Identity Based on Password Tokens for Network Security Technology” (GB/T 43779-2024, referred to as “Trusted Communication”). The North American mandate of the TRACED ACT is also very technically specific in targeting STIR/SHAKEN implementation.
In Europe, only France, with the “Neagelen” law, follows the North American model by imposing a version of the STIR/SHAKEN framework with some peculiarities at the governance level. These frameworks have in common that they require a PKI (public key infrastructure), which demands a significant level of coordination due to the figure of the principal trusted agent, in other words, the one who acts as a trusted agent assuming the role of certifying entity.
Precisely one of the clearest differences between these architectures is who assumes this trusted role. China opts for direct state control, the USA for greater openness towards a limited group of private entities (although they ultimately answer to a regulator). France, for its part, positions itself as a centralized model of state control (in this respect closer to China than to the US).
From the perspective of Branded Calling, the Chinese model truly seeks to identify the person making the call, which in itself already overcomes some assumptions about individual privacy that would not be easy to transfer to Europe. In terms of user experience, China allows up to five different profiles per device (for example, a personal profile and another as a company employee), and the interface can display photographs, videos, links to certificates, or personal data such as job title, postal address, company employed, etc.
The FCC mandate on STIR/SHAKEN only regulates the authentication/verification of calls on the network, that is, it tells you if the origin of the call is reliable and that the information has not been manipulated during transport, but it does not refer to the RCD, which is what enables branded calling in this case. In this context, the CTIA (Cellular Telephone Industries Association) has positioned its Branded Calling ID ecosystem as the de facto standard, positioning SecureG as the sole CA for branded calls and its associates in various roles necessary for vetting, onboarding, and digital signature processes.
Regulation based on anti-fraud goals
European countries have based a large part of their strategy against fraud and spam on strengthening their regulation against these abuses. The predominant technological measure is centralized numbering databases that allow operators to filter valid traffic from that which is not. These databases are usually national in nature and respond to the different strategies adopted by the country (e.g., Do-not-originate lists, roaming users, etc.).
The telecommunications market in Europe has as its general framework the European Electronic Communications Code (EECC). The EECC covers aspects such as authorizations and licenses, use of the radio frequency space, end-user rights, numbering, Network security and resilience… Establishing a framework of obligations that are specified in the transposition into national legislation by each Member State.
The obligations of electronic communications operators include:
- Maintaining confidence in the identity of broadcasts.
- Ensuring an adequate level of security.
- Preventing and identifying security incidents, including measures to detect spoofing. Identity theft, fraudulent use of numbers, unauthorized access.
Dominant strategies against phone fraud in Europe
With varying levels of penetration depending on the country, the dominant strategies for protecting telephone network users in Europe are:
- Registration of non-originated numbers (Do-not-originate registry): A database of numbers that can never be used to make outgoing calls.
- Protected Numbers Registry: A list of phone numbers that have not been assigned by the National Regulatory Authorities (NRAs) and that cannot be used to originate calls.
- Incoming International Call Blocking with a National Number as the CLI: Calls originating from abroad that use a national number as the CLI are blocked.
- Sender ID (SMS) Registration or Banning: Legitimate companies sometimes send SMS messages. that display their business name as text instead of a phone number. Regulators may ban these formats entirely or allow only SMS with legitimate sender IDs from a registry.
- STIR/Shaken: Only in France, formally dropped after public consultations in the UK and Ireland, mainly for economic reasons, IP network penetration, and lack of effect on international calls (the main source of fraudulent calls).
Branded calling in light of European Union legislation
The European standard and the various transpositions that member countries make of it into their own regulations focus on obliging operators to limit the possibility of fraud. It does not impose specific technological solutions, although in some cases countries do participate in the design of some of them (e.g., Ireland, through ComReg, participates in the design of the Voice Firewall). The obligation to correctly identify commercial communications is expressed in standards that regulate the use of certain numbering ranges (for example, in Spain, the 800/900 ranges) or lists of authorized aliases for sending commercial communications via SMS.
Since an in-band digital signature system such as STIR/Shaken (or other alternatives such as VVP is not defined, it is also not possible to articulate the use of Rich Call Data or any other mechanism for transporting information in addition to the telephone number, with full guarantees that they will not be subject to spoofing. The avenues left open by the lack of specific regulation for the development of branded calling in Europe are:
- Private ecosystems participated in by the main operators: associations of industry players that achieve sufficient traction to position a branded calling architecture with sufficient market penetration (similar to the US CTIA initiative).
- Out-of-band solutions: that can securely transport brand information to the final party.
- Applications mobile: whether dedicated applications (e.g. antispam apps, dialers) or integrations of communications capabilities into existing apps.
Branded Calling
Quobis supports carriers and enterprises in designing their branded calling strategy and deploying and maintaining the architecture that supports it.

